Thycotic Secret Server stands as a robust solution for safeguarding your organization’s most sensitive information, including passwords, SSH keys, and certificates. This comprehensive platform addresses the critical need for privileged access management (PAM), ensuring that only authorized individuals have access to critical systems and data.
The Thycotic Secret Server solution is designed to simplify and streamline the process of managing privileged accounts and secrets. By centralizing access control and automating password rotation, Thycotic Secret Server empowers organizations to reduce security risks, enhance compliance, and improve operational efficiency.
Auditing and Reporting

Thycotic Secret Server provides comprehensive auditing capabilities to track and monitor user activity, access attempts, and password changes. These logs and events help organizations meet compliance requirements, identify security threats, and ensure accountability.
Generating Reports
Reports can be generated on various aspects of user activity, including access attempts, password changes, and privilege assignments. The reporting engine offers customizable templates and filters to create reports that meet specific needs.
- User Activity Reports: These reports track user logins, password changes, and access to secrets. They can be used to identify suspicious activity, such as multiple failed login attempts or unauthorized access.
- Access Attempts Reports: These reports show all attempts to access secrets, including successful and failed attempts. They can be used to identify patterns of unauthorized access or potential security breaches.
- Password Change Reports: These reports track all password changes, including the date and time of the change, the user who made the change, and the new password (if enabled). They can be used to ensure compliance with password policies and identify potential security risks.
Security Audits and Reports, Thycotic secret server
Thycotic Secret Server enables organizations to conduct comprehensive security audits and generate reports that demonstrate compliance with industry standards and regulations.
- Privilege Audit Reports: These reports provide an overview of user privileges and access to secrets. They can be used to identify potential security risks associated with excessive privileges or inappropriate access.
- Password Complexity Audit Reports: These reports analyze password complexity and identify passwords that do not meet defined security standards. They can be used to ensure compliance with password policies and reduce the risk of password compromise.
- Secret Access Audit Reports: These reports track access to secrets and identify users who have accessed specific secrets. They can be used to investigate security incidents and identify potential insider threats.
Closure: Thycotic Secret Server
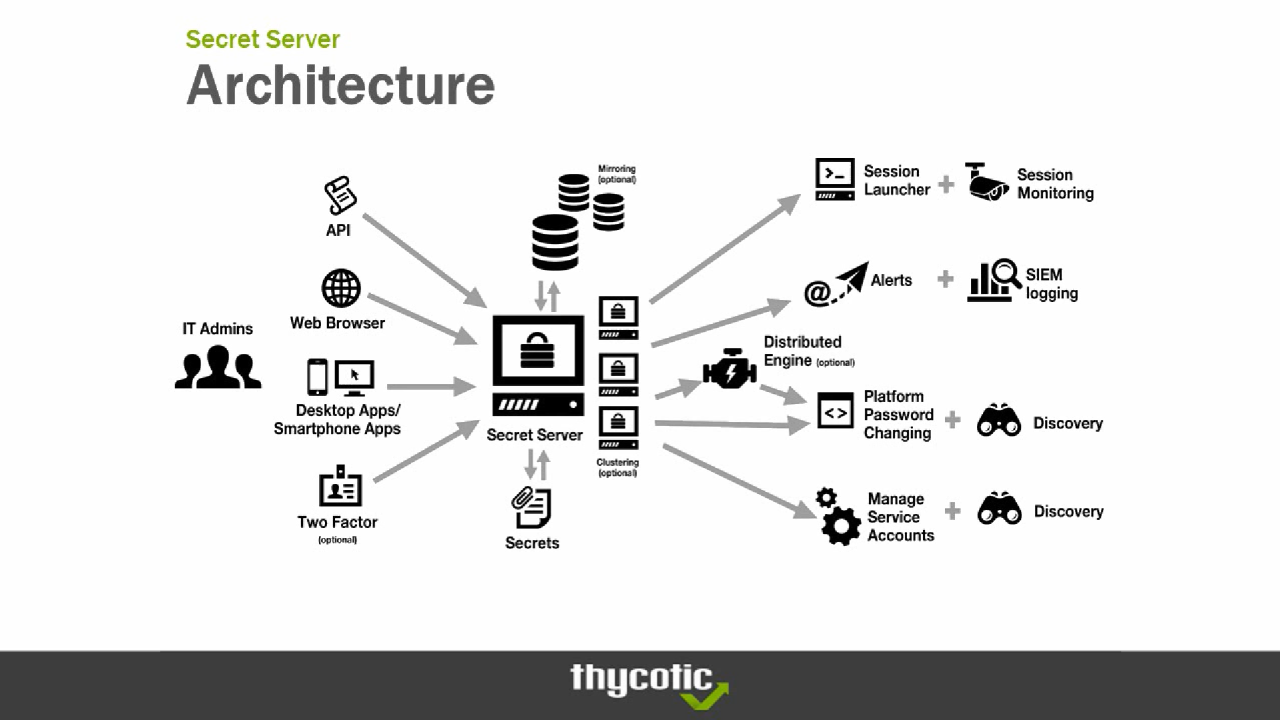
With its powerful features, comprehensive security measures, and seamless integration capabilities, Thycotic Secret Server provides a comprehensive approach to privileged access management. By implementing Thycotic Secret Server, organizations can gain peace of mind knowing that their sensitive data is protected, their compliance obligations are met, and their operational efficiency is optimized.
Thycotic Secret Server is a powerful tool for managing and securing privileged credentials. It’s often used in conjunction with SQL Server , as many organizations store sensitive data within SQL Server databases. By integrating Thycotic Secret Server with SQL Server, administrators can ensure that access to these databases is tightly controlled and auditable, enhancing overall security posture.
